Pentesting Report Template
Pentesting Report Template - Web a penetration testing report is a document that details the findings of a security assessment conducted using penetration testing techniques. Web penetration test report megacorp one august 10th, 2013 offensive security services, llc 19706 one norman blvd. Report is following dread model. Web what is a pentest report? Great content to learn about penetration testing methodologies and techniques. Web a penetration tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Our pentest report templates work out of the box. Tips for creating a strong cybersecurity assessment report; Writing a penetration testing report;. There is a possiblity of some.
Customizable and reusable templates for findings. The objective is to identify problem areas and implement a solution. A basic penetration testing report template for application testing. There is a possiblity of some. Tips for creating a strong cybersecurity assessment report; Web a penetration testing report is a document that details the findings of a security assessment conducted using penetration testing techniques. Web a penetration test report provides a comprehensive summary of the system’s vulnerabilities. Take on the role of penetration tester for the. Web never start from scratch. Download individual and aggregated reports in just a few clicks.
A pentest report should involve the following areas: Pentest report structureblack, grey and white box penetration testingpentesting project phases public pentest reports follow the links to see more. Base latex template for a penetration. Web writing a penetration testing report is an art that needs to be learned to make sure that the report has delivered the right message to the right people. There is a possiblity of some. In addition, it includes recommendations for patching, hardening, and restricting the functionality of systems when necessary. Web we offer a platform that lets you create and format reporting templates with ease, facilitates communication between you and the client, and organizes every step of the pentesting. Web the below links provide more guidance to writing your reports. Web penetration test report megacorp one august 10th, 2013 offensive security services, llc 19706 one norman blvd. Web a penetration test report provides a comprehensive summary of the system’s vulnerabilities.
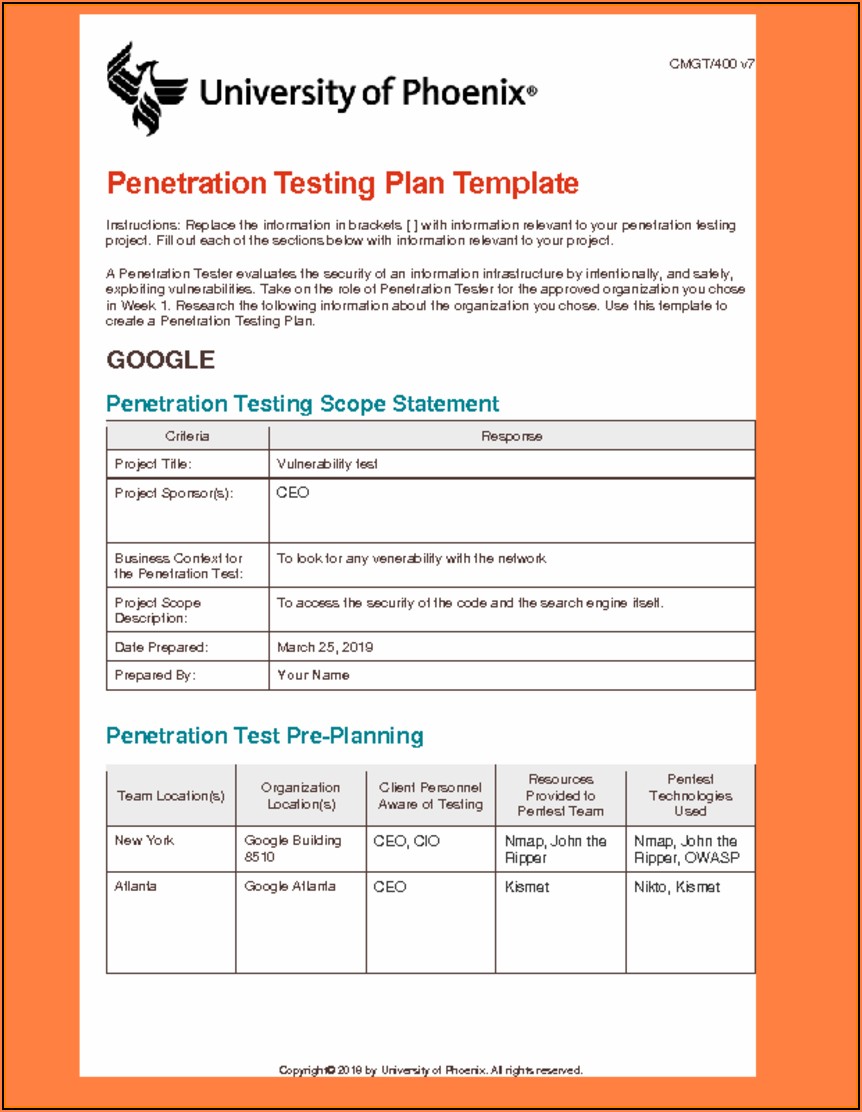
Pentesting Report Vulnerability Test
Web what is a penetration testing report? Web the below links provide more guidance to writing your reports. Great content to learn about penetration testing methodologies and techniques. Web a good vulnerability assessment report aims to provide network security engineers insights into system vulnerabilities with an end goal of empowering the. In addition, it includes recommendations for patching, hardening, and.
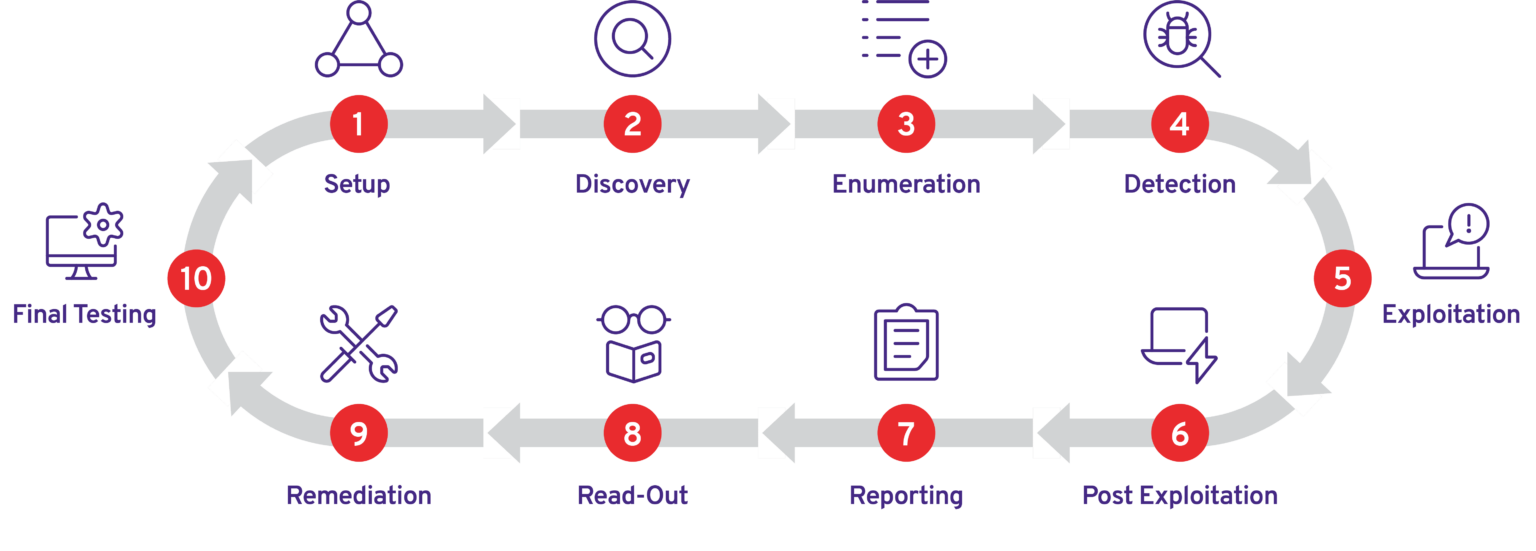
Hack the 10 Steps of the Pentesting Routine PlexTrac
In addition, it includes recommendations for patching, hardening, and restricting the functionality of systems when necessary. Web what is a pentest report? Web a penetration test (ethical hacking) can be defined as an authorized cyberattack launched as part of a security audit to look at the system from a hacker’s. Our pentest report templates work out of the box. Take.
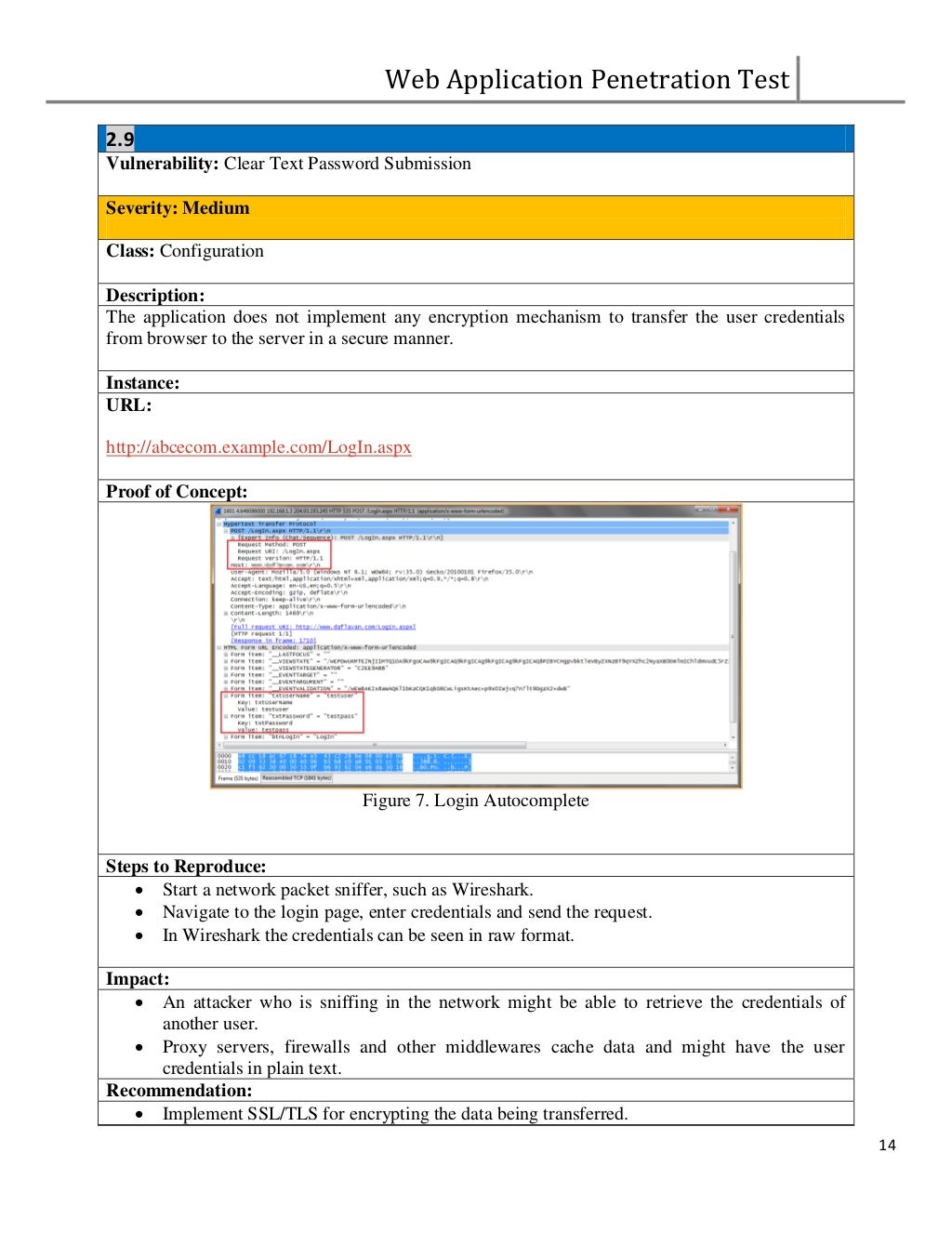
Web PenTest Sample Report
A basic penetration testing report template for application testing. Web a penetration tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. In addition, it includes recommendations for patching, hardening, and restricting the functionality of systems when necessary. Web we offer a platform that lets you create and format reporting templates with ease, facilitates communication between.
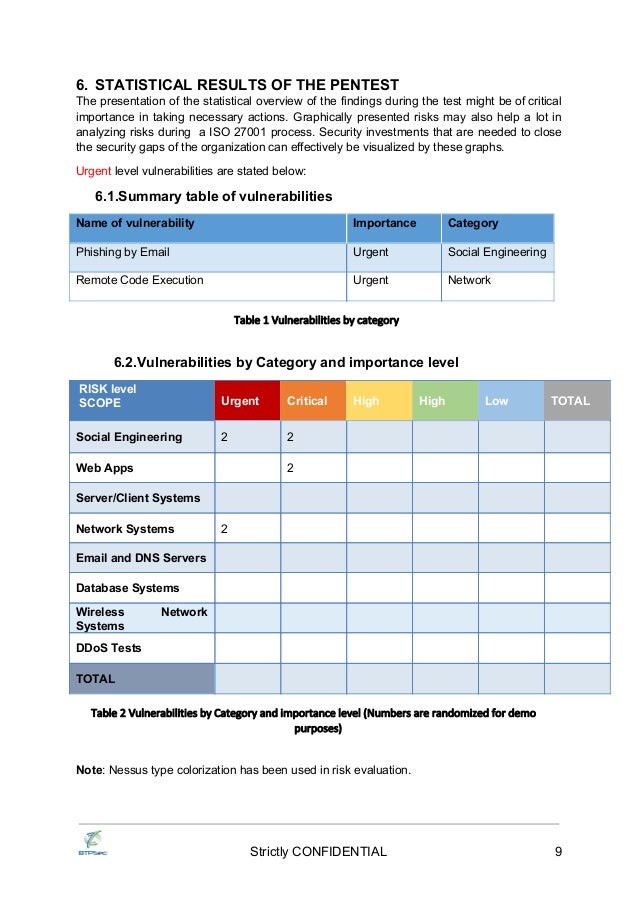
Btpsec Sample Test Report
The objective is to identify problem areas and implement a solution. Web what is a pentest report? A pentest report should involve the following areas: Web a penetration tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Web download pentest report templates.
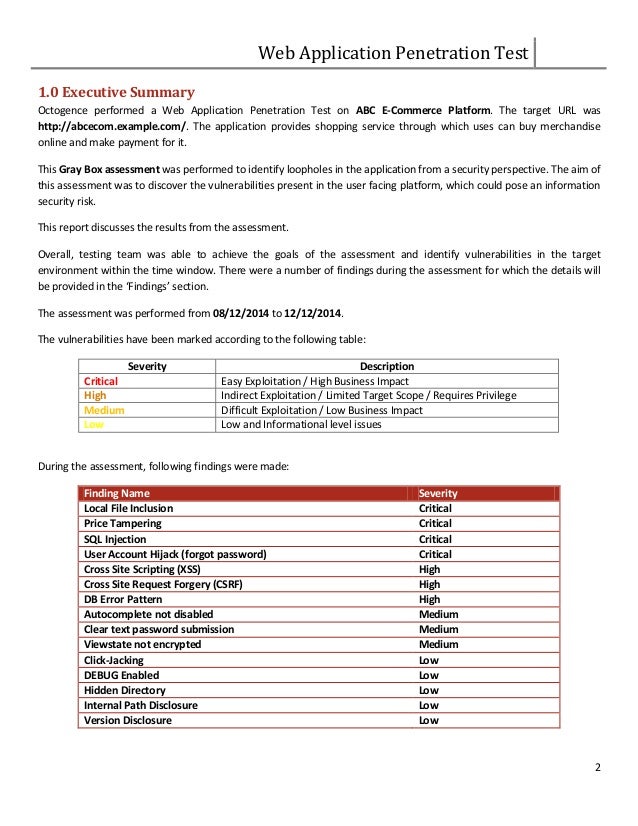
Test Report 2013
Customizable and reusable templates for findings. A pentest report should involve the following areas: Take on the role of penetration tester for the. Download individual and aggregated reports in just a few clicks. Our pentest report templates work out of the box.
Test Report Template Doc PDF Template
Our pentest report templates work out of the box. Web penetration test report megacorp one august 10th, 2013 offensive security services, llc 19706 one norman blvd. The objective is to identify problem areas and implement a solution. Great content to learn about penetration testing methodologies and techniques. Complete templates of issues, cwe, cve, mitre att&ck,.
Application Pentest
Web the below links provide more guidance to writing your reports. Web download pentest report templates. Web a good vulnerability assessment report aims to provide network security engineers insights into system vulnerabilities with an end goal of empowering the. Our pentest report templates work out of the box. The objective is to identify problem areas and implement a solution.
Vulnerability Assessment And Testing Plan Templates
Web a penetration tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Web use templates for full reports or individual findings and engagements. An outline of risk exposure for the tested assets; Great content to learn about penetration testing methodologies and techniques. Web what is a penetration testing report?
Web PenTest Sample Report
Web a penetration tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Web what is a penetration testing report? Writing a penetration testing report;. Web penetration test report megacorp one august 10th, 2013 offensive security services, llc 19706 one norman blvd. Choose the predefined template you need or create your own template to reuse every.
Pentest Report Sample
Web what is a penetration testing report? Web we offer a platform that lets you create and format reporting templates with ease, facilitates communication between you and the client, and organizes every step of the pentesting. Web a penetration testing report is a document that details the findings of a security assessment conducted using penetration testing techniques. Web a penetration.
Our Pentest Report Templates Work Out Of The Box.
The objective is to identify problem areas and implement a solution. Take on the role of penetration tester for the. Choose the predefined template you need or create your own template to reuse every time. In addition, it includes recommendations for patching, hardening, and restricting the functionality of systems when necessary.
Web The Below Links Provide More Guidance To Writing Your Reports.
Complete templates of issues, cwe, cve, mitre att&ck,. Suite b #253 cornelius, nc 28031 united states of america Penetration testing (pentesting) involves assessing the security of a system, network, or application. Writing a penetration testing report;.
Report Is Following Dread Model.
Web a penetration tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Web download pentest report templates. Web penetration test report megacorp one august 10th, 2013 offensive security services, llc 19706 one norman blvd. Web curated list of pentest reports from various security companies and individuals.
Base Latex Template For A Penetration.
Web penetration testing report template. Customizable and reusable templates for findings. Web a penetration test (ethical hacking) can be defined as an authorized cyberattack launched as part of a security audit to look at the system from a hacker’s. An outline of risk exposure for the tested assets;